The Zero Trust Approach to Modern Network Security
Zero Trust Network Access (ZTNA), commonly enabled via creating a Software Defined Perimeter (SDP), provides businesses of all sizes an easier, more secure way of allowing employees to access data from wherever they are, regardless of where the data is living. This modern way of securing a corporate network addresses two major trends in network security: […]
Author
Date
Category
All Categories
- AI-powered security
- Attacks & Threats
- Cybersecurity
- Hybrid Cloud
- Network
- Network Firewall
- Network Protection
- News
- Remote Workforce
- Security
- Zero Trust
Contents
Popular Posts
Product
Join the Newsletter
Zero Trust Network Access (ZTNA), commonly enabled via creating a Software Defined Perimeter (SDP), provides businesses of all sizes an easier, more secure way of allowing employees to access data from wherever they are, regardless of where the data is living.
This modern way of securing a corporate network addresses two major trends in network security:
1) Employees and 3rd parties with access privileges are working from anywhere using their laptops, tablets & mobile devices.
2) Business critical data is now living in hosted SaaS applications, servers in AWS, Azure, GCP, and on-premise in servers behind the firewall.
These two trends have moved the goal post for securing the modern network. First and foremost, the security perimeter is no longer isolated to the office walls behind the safety of a firewall. ZTNA at its core says that security must be based on the user.. Not a physical location, subnet or specific device.
Implementing Zero Trust within your organization may sound like a complicated task. Fortunately, due to technological advancements, achieving this can be simple.
This article will break down the principles of Zero Trust, how it may apply to your business, the benefits of implementing ZTNA for both users and administrators, and why legacy systems are no longer enough.
7 Principles of Zero Trust
It’s important to note that no matter if it is a 5 employee small business or a 5,000 employee enterprise, the shift to adopt Zero Trust principles is happening within all sectors of business.
The 7 principles below were outlined by the United States, Department of Defense:
-
The User
It all starts with the user and the motto “Never Trust, Always Verify”. Continuously authenticate, assess, and monitor user activity to govern users’ access and privileges while protecting and securing all interactions.
-
Device
Understand the health and status of devices to inform risk decisions. Real time inspection, assessment and patching informs every access request.
-
Application & workload
Secure everything from applications to servers, to include the protection of containers and virtual machines.
-
Data
Data transparency and visibility are enabled and secured by enterprise infrastructure, applications, standards, robust end-to-end encryption, and data tagging.
-
Network & environment
Segment, isolate and control (physically and logically) the network environment with granular policy and access controls.
-
Automation & orchestration
Automate security response based on defined processes and security policies enabled by AI. Example: blocking actions or forcing remediation based on intelligent decisions.
-
Visibility & analytics
Analyze events, activities and behaviors to derive context and apply AI / Machine Learning to achieve a highly personalized model that improves detection and reaction time in making real time access decisions.
Applying Zero Trust Network Access (ZTNA) to The Modern Business
High-level Timus ZTNA Architecture
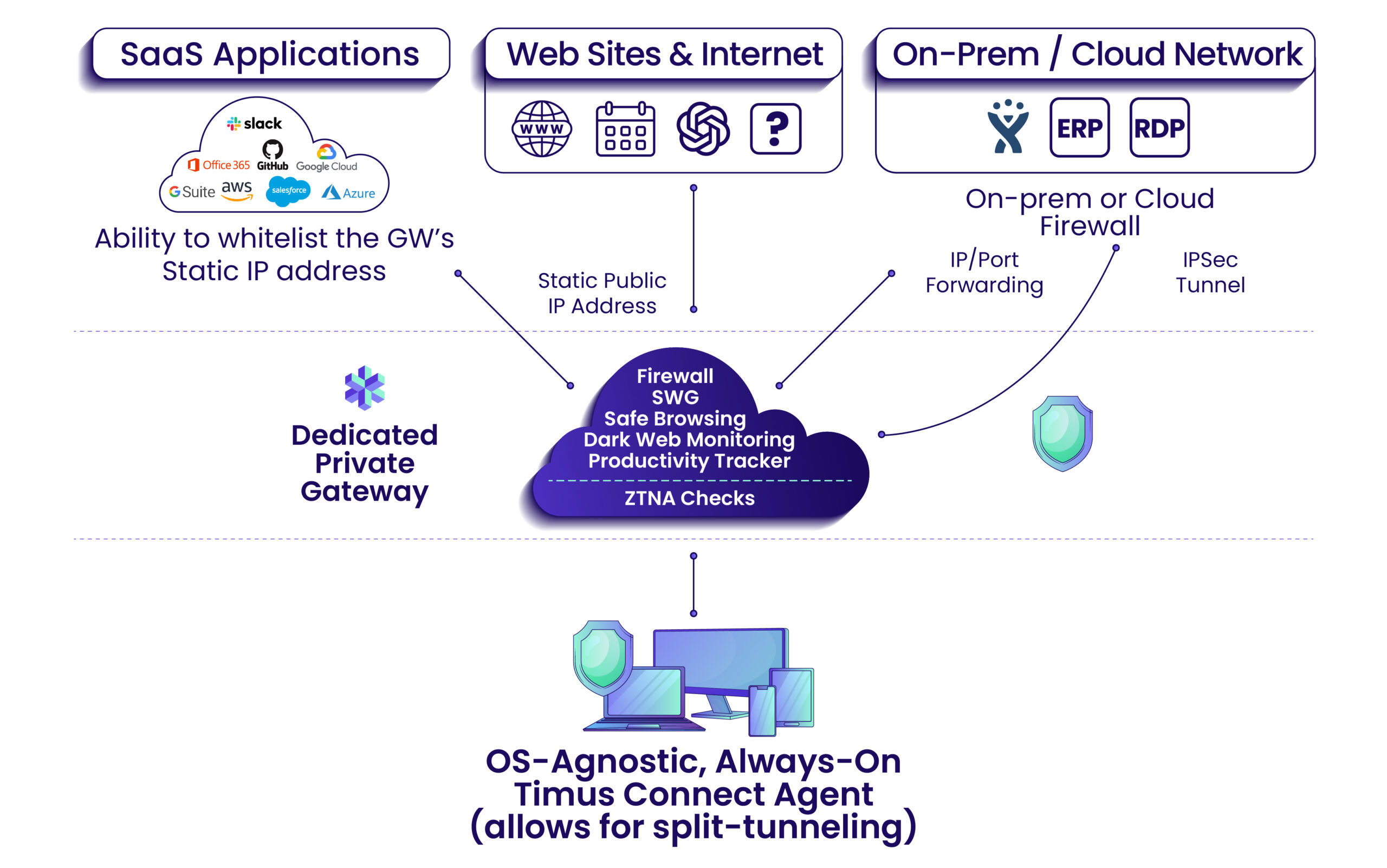
Using the identified 7 pillars to accomplish Zero Trust Network Access, the above diagram covers each pillar in a simplified visual which outlines the four core sources of ways users access data (open web, SaaS applications, hosted servers, and on-premise resources)
How is this different from legacy systems?
With legacy systems such as VPNs stemming from the on-premise firewall, once proper credentials are inputted, the user gains lateral access to everything within the subnet. This route of connectivity is manual for the user, manual to configure for administrators, and only provides access to the physical office.
Zero Trust Network Access provides an always-on agent for users with conditional access policies to ensure the user is who they say they are, scanning for key behavioral analytics which would indicate that the person attempting to login, isn’t who they claim to be.
Once connected & within the software defined perimeter, granular permission based controls surround the user, not the device while providing one agent to connect to all mission critical business applications.
Conditional Access based on Behavioral Analytics
Timus has one of the richest sets of zero-trust behavioral checklists before it grants access to a user. Starting from the entry point, some key behavioral analytics to look for are: New device, Out of Radius, New Country, Impossible Travel, Untrusted IP, and Breached Email-Address.
If a behavior leading the policy engine to believe that this may not be who they say they are is triggered, multi-factor authentication (MFA) customized to the level of risk will be forced at which point they can gain access to the network, or be banned / blocked / denied.
Dedicated Gateway Acting as a Cloud Firewall
The invention of the cloud firewall via a dedicated gateway, such as what Timus does, is ultimately what makes this all possible. This is the piece that ties this all together… Is a building more secure with 10 doors to entry or one? The answer is one.
The dedicated gateway should be exclusive to the corresponding business and provide a dedicated, static IP address for users to connect through. Whether it’s a server in Azure, a SaaS app such as Sharepoint, OneDrive, a PaaS developer tool, or hypervisor on-site.
The dedicated gateway will be the single lane highway for users to connect.
SaaS Applications
Create a layered approach to conditional access via whitelisting the dedicated static IP address, ensuring that even in the event of a phishing attack or credentials being stolen- if the user is not connecting through the static IP, even if they have the correct login and password, access will not be granted.
Open Web
Back to the layered security approach, having an antivirus, endpoint protection, EDR & MDR… What do these all have in common? 1) They’re security tools. 2) As tools, they operate as agents within the operating system and take up precious resources on the end-user devices.
Creating web filtering rules at the network layer within the cloud firewall not only preserves resources on the managed devices, but ensures that users are not accessing data which is unproductive and harmful for consumption.
Cloud Servers
Digital transformation has made scaling servers outside the server room easy. Providers such as Microsoft, Google, and Amazon allow for companies to host private virtual machines within their data centers on a per customer basis.
In order to protect these servers, yet another VPN or agent is required to restrict access.
Leveraging a cloud firewall will allow for IPsec tunnels directly from the dedicated gateway to the server hosted in AWS, Azure, GCP creating connectivity based on the user to these resources, leveraging one agent.
On-Premise Resources
Although it is likely that less & less data is hosted within the office & server room, resources remain and the need for an on-premise firewall is still there along with a route for users to connect into the office.
Similar to AWS or Azure, creating an IPsec tunnel to the firewall on site, from the gateway will allow for connectivity based on the user via granular user based permissions.
Benefits to Users & Administrators
Users
Users will be users as IT admins say. For the user, productivity and ease of use are top of mind. We all have a job to do right?
Legacy systems created multiple logins, slow speeds, confusion as to which systems require which credentials and on top of all of that, the security landscape has owners and employees nervous to click, visit and leverage their devices to the fullest extent.
With ZTNA, the user simply authenticates and can access data no matter where it lives.
Administrators
Administrators need to wear many hats each day. Protecting the environment is priority number one. Adding Zero Trust Network Access to the corporate environment provides admins with significantly improved visibility of the network.. SaaS applications are great, except from the visibility perspective.
Visibility, scalability and automation are the words to win over any IT admin. While users will be users, having a solution to deploy across the environment which gives the employees one agent to connect to each system, with detailed logs, reporting and response mechanisms will enhance security but also make an admin sleep better at night knowing that their users can work in a productive and protected state.
Conclusion
Whether a small 4 person business or a large enterprise, the pain points around remote access for users have clear parallels. Implementing Zero Trust Network Access for your businesses approach to network security will enable teams to work from anywhere with peace of mind. With the security perimeter now wherever the user is, the layered security delivery must follow this same approach… Your users, devices, insurance provider, compliance officers, and your data itself will thank you.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.
