Why ZTNA is a Better Choice than VPNs for Remote Access
Zero Trust Network Access… We’ve all probably heard the term at some point in recent months with all the buzz it’s been getting. It seems that everyone has a different definition of it. What does it mean? And why is it so consistently compared to VPNs? What is a VPN? There are a lot of […]
Author
Date
Category
All Categories
- AI-powered security
- Attacks & Threats
- Cybersecurity
- Hybrid Cloud
- Network
- Network Firewall
- Network Protection
- News
- Remote Workforce
- Security
- Zero Trust
Contents
Popular Posts
Product
Join the Newsletter

Zero Trust Network Access… We’ve all probably heard the term at some point in recent months with all the buzz it’s been getting. It seems that everyone has a different definition of it. What does it mean? And why is it so consistently compared to VPNs? What is a VPN? There are a lot of questions to ask. We’ll be exploring the answers to all of them as we discuss the pros and cons of VPNs, and what exactly Zero Trust means as it relates to remote access.
What is a VPN?
VPNs (Virtual Private Networks) are a form of remote access in which traffic is sent over an encrypted channel from one location to another. While most people are familiar with consumer-grade VPNs, there are several types and flavors:
- Client-Site
The Client-Site VPN is a form of business remote access where a person can connect to their corporate network from wherever they are through a VPN client software. This typically requires some kind of configuration on the users’ end to map it to their particular network. This is also the type of VPN that we will be focusing on when comparing to ZTNA.
- Site-to-Site
Site-to-site VPNs are another form of business VPN where businesses can connect the local networks of their branch offices to their headquarters. More recently, this has extended to cloud environments to have resources stored offsite more easily accessible.
- Personal VPN
Personal VPNs, or commercial-grade VPNs, are the type most commonly thought of when people say “VPN.” With personal VPNs, a VPN company will host servers all over the world and allow the average consumer to connect to them for the purpose of online privacy and added personal security.
What is ZTNA?
ZTNA, or Zero Trust Network Access, is a philosophy of network security in which the identity of a user is never assumed to be legitimate. This is expressed by the phrase and principle of “never trust, always verify.”
While the implementation of ZTNA principles is constantly evolving and can mean several different things to different organizations, the basic principles can be condensed to those outlined by Forrester:
- All Entities on a Network Must be Considered Untrusted By Default
When a user, device, or service attempts to access the network, it should be assumed that the entity is actually an illegitimate entry attempt by a hacker. If these entities are all hackers, there must be controls in place to stop unauthorized attempts in their tracks, while also maintaining availability for legitimate users.
- Least Privilege Must be Enforced
Least Privilege as a concept deals with the level of access a user has to a set of resources. If a user’s job only requires them to have access to one file on a server, they shouldn’t be able to open or even see the other stuff.
In terms of zero trust, users should only be able to access what they need in order to accomplish their job role. Everything else is both unnecessary and a security risk. Least privilege does not allow lateral movement within the network.
- Comprehensive Monitoring
Of course, all of this is negligible without appropriate monitoring and notifications. In order to refine zero trust processes, traffic logs and user sign-in events must be easily visible by administrators. This way, if controls are too tight or loose, they can be adjusted accordingly based on relevant data.
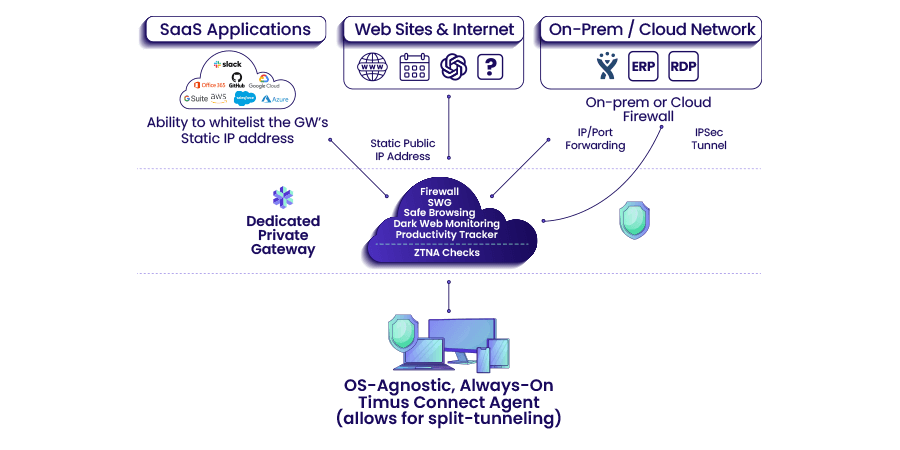
Feature Face-Off: ZTNA vs VPN
Based on the criteria above, let’s look at how traditional VPNs stack up when it comes to security.
I don’t want to be too cruel to VPNs because they’ve done a lot for the evolution of remote access, so I’ll start it out with a win. We can look back on dial-up and recognize all it’s done and still choose to not settle for 400kB of bandwidth. Game recognizes game.
VPNs do allow for comprehensive monitoring in the sense that if I’m connected to a VPN, all of that traffic is visible from the firewall/VPN server. I can see who is signing in and also what they’re accessing when that traffic hits the headquarters.
The problem with this being that VPN credentials are constantly being sold on the dark web. Even as I’m writing this, someone’s VPN credentials are being stolen and allowing even the most amateur of hackers to break into a company’s internal network. In this sense, all entities on a network are being considered trusted.
On that note, what happens when a user, legitimate or otherwise, gets into the network? What will they be able to see? Well, I can tell you that especially with quick and easy VPN configurations, the entire network is visible by those connected to the VPN. Once the user is assigned an internal IP, every other IP on that network will be reaching out, saying “hey,” asking to talk. In zero-trust terms, least privilege is not being enforced. Any user can move laterally anywhere within the network.
Authentication vs Authorization: Key Differences
If VPNs can handle that comprehensive monitoring, ZTNA can be shaved down with Occam’s Razor to a hardening of authentication and authorization.
Authentication can be described as the verification of identity. VPNs will either take some kind of username and password or certificate key; both of which can be easily stolen. Key management techniques have their merits, but Torvalds forbid someone breaks in, it’s over. The entire network is compromised. The concept of authentication is hardened by the zero-trust principle of untrusted entities, which puts periodic checks in front of user verification, such as which device they’re using, where their sign-in location is, and even behavioral analysis.
Authorization, by contrast, relates to the kind of access a user has once they make it into the network. If a user or hacker makes their way behind the castle walls, which rooms do they have keys to? What can they edit? What can they compromise? This doesn’t just consider hackers, but insider threats as well. Disgruntled or poorly trained employees can do just as much damage as an outside attacker. The zero-trust principle of least privilege concerns itself with this level of granular access. If the hacker, employee, employee’s neighbor who saw an open laptop, etc. can’t see it, they can’t leak it or delete it.
Business Operations: Impact of Remote Access Solutions
Heavy is the head that wears the crown of IT purchasing. Settling on a remote access tool could be the difference between calm and calamity. There are several types of remote access solutions.
When making such a heavy decision, there are several things to keep in mind.
- Cost
For an SMB, cost is probably top priority. Solutions like VDI and DaaS are likely not the most conducive option for the sheer fact that solutions like these take into account infrastructure and maintenance costs. While DaaS and VDI are certainly secure options, VPN-like solutions just check the more cost-effective box.
- Flexibility
Not to keep kicking VDI while it’s down, but it also lacks the flexibility of other remote access solutions. It can be used on BYOD and managed devices alike, sure, but it is also heavily dependent on the internet connection of the end-device to be able to stream an entire desktop’s worth of content. Imagine if your work day depended on your ability to stream a movie on Netflix. It’s the same principle.
- Security
With VDI and DaaS being kicked as it was in the previous two, we’re left with VPNs and ZTNA. As we’ve previously discussed, VPNs just don’t have the level of granularity and intelligence when it comes to identity verification that ZTNA has.
Choosing the Right Path: ZTNA or VPN?
With all that we’ve gone over, it seems that the path ahead is clear. As mentioned before, we would never knock dial-up for what it was when it came out! It revolutionized internet connectivity on the global scale. We can praise it without feeling the responsibility to keep using legacy technology. ZTNA is the next evolution of remote accessing, building on what its predecessors brought to the industry.. It deserves respect, not storage on my device.
FAQ
VPNs encrypt and encapsulate traffic, sending it over a secure channel to its ultimate destination. For all intents and purposes, VPN traffic seems as though it is originating from the headquarter network when it reaches its destination. Only the client device and the VPN server know the truth.
ZTNA as a philosophy and framework favors security over availability. While this may sound like it can make the users’ lives worse to put a smile on a sadistic admin, Timus has found a balance with adaptive policies that only trigger when our controls pick up on something out of the ordinary.
ZTNA gives the administrator greater control over the sign-in process and less entry-points for unauthorized users to break into the network. With Timus ZTNA, this is accomplished through our rich behavior set and sign-in policies that seamlessly allow access for legitimate users and block/control access for those that indicate higher risk.
Because Timus ZTNA controls are based in the cloud, scalability is not only possible, but by design. Blanket controls can be made for the entire organization with more granular rule options as needed.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.
