How to Prevent Hackers from Weaponizing Your Tools Against You: Learnings from the ConnectWise ScreenConnect Breach
Connectwise said Tuesday that “A critical ConnectWise ScreenConnect vulnerability that puts thousands of servers at risk of takeover is actively being exploited in the wild”, sending shockwaves across the Managed Service Providers (MSPs) using ScreenConnect to gain remote access to customer endpoints for services such as IT support. This critical flaw, tracked as CVE-2024-1709, makes it […]
Author
Date
Category
All Categories
- AI-powered security
- Attacks & Threats
- Cybersecurity
- Hybrid Cloud
- Network
- Network Firewall
- Network Protection
- News
- Remote Workforce
- Security
- Zero Trust
Contents
Popular Posts
Product
Join the Newsletter

Connectwise said Tuesday that “A critical ConnectWise ScreenConnect vulnerability that puts thousands of servers at risk of takeover is actively being exploited in the wild”, sending shockwaves across the Managed Service Providers (MSPs) using ScreenConnect to gain remote access to customer endpoints for services such as IT support.
This critical flaw, tracked as CVE-2024-1709, makes it “trivial and embarrassingly easy” to achieve authentication bypass and gain administrative access to a ScreenConnect instance, according to researchers at Huntress.
The second bug, tracked as CVE-2024-1708, is a path traversal vulnerability that could allow a malicious ScreenConnect extension to achieve remote code execution (RCE) outside of its intended subdirectory.
“There’s a reckoning coming with dual-purpose software; like Huntress uncovered with MOVEit over the summer, the same seamless functionality it gives to IT teams, it also gives to hackers,” said Huntress CEO Kyle Hanslovan. “With remote access software, the bad guys can push ransomware as easily as the good guys can push a patch. And once they start pushing their data encryptors, I’d be willing to bet 90% of preventative software won’t catch it because it’s coming from a trusted source.”
Attackers have already been exploiting the vulnerability to breach unpatched ScreenConnect servers and deploy LockBit ransomware payloads on compromised networks.
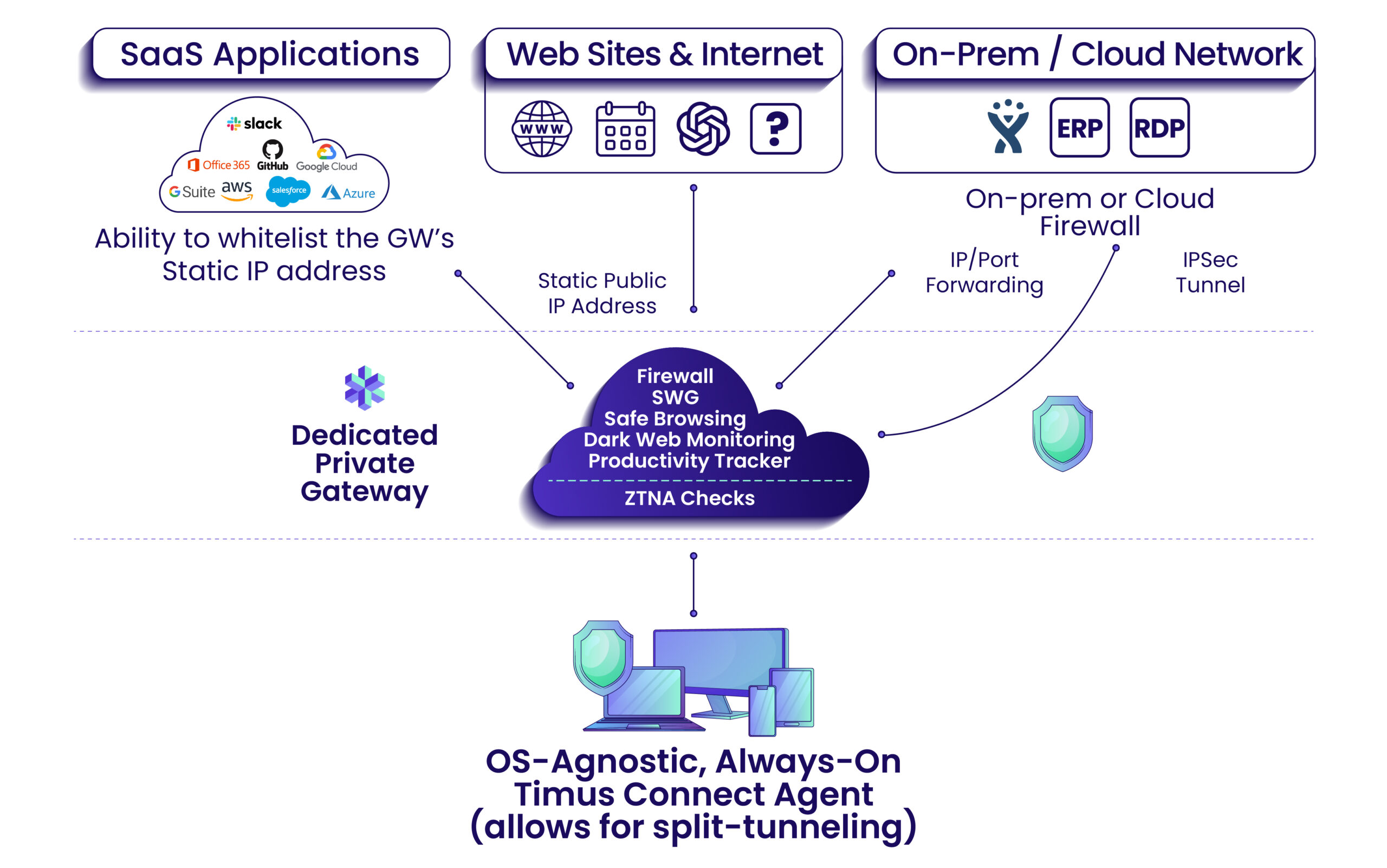
While no one can prevent breaches 100% of the time (remember the old adage “it’s not a matter of if, but when”), MSPs can and should work on minimizing their attack surface in order to prevent brute force attacks against themselves and their clients. Below, we show you one such way to lock down access to your RMM, PSA, documentation tools and many other business SaaS apps via allowlisting the dedicated Timus Static IP address.
Bad Actor + Stolen Credentials + Timus = Unsuccessful Breach
The approach to security in 2024 is one which must be layered. Enforcing conditional access to all sources of mission critical data has risen to the forefront. Timus Zero Trust Network Access ensures that when users connect to the corporate network, identity verification is cross referenced based on a customized set of behaviors to ensure that first and foremost, the user is in fact who they claim to be.
Timus does not stop there however. Once authenticated, rather than connecting directly to mission critical resources, users first pass through a dedicated private gateway with a static IP address. This private, encrypted tunnel acts as the security buffer between the user and resources within the environment.
Allowlisting this IP address within your critical applications ensures that credentials alone do not grant access, effectively minimizing your attack surface from an ever changing scramble of IPs to a single static IP and single point of entry to the network. Securing a building with a single path of entry is much more manageable than one with dynamic, ever changing paths to get inside.
Effectively acting as your cloud firewall, Timus SASE takes conditional access to new heights through private, encrypted tunnels between the dedicated cloud gateways and the company’s public and private servers, on-prem or in the cloud.
The reality is, bad actors have found ways to stay ahead and fortunately methods to mitigate risk have also adapted. Timus enables MSPs and their clients to sleep at night by stopping disaster before it strikes. Brute force attacks, phishing & the many other complex ways of gaining access to your tools are going to continue. Stay ahead and ensure your tools are not weaponized against you.
Timus SASE Architecture
The Path Forward
In the face of increased attacks and technological advances available to bad actors, MSPs can minimize their risks and exposure to themselves and their clients by reducing their attack surface to brute force attacks. One of the best ways is locking access to resources via a single point of network entry. This can be done through the dedicated Timus cloud-based firewall with its Static IP address, acting as a security buffer and a sole point of entry into corporate resources and business SaaS apps.
FAQ
The vulnerability in ConnectWise ScreenConnect was a critical security flaw that allowed attackers to bypass authentication measures. This meant unauthorized users could potentially access and control remote systems, steal sensitive data, or deploy malware without detection.
Businesses using the compromised version of ScreenConnect risked unauthorized access to their IT infrastructure. This could lead to data breaches, financial loss, operational disruption, and damage to their reputation due to potential exposure of confidential information.
The Timus SASE solution, grounded in the Zero Trust model, ensures that every access request to the network is thoroughly authenticated and authorized. In addition, Timus provides a dedicated gateway to each client, protected by an adaptive cloud firewall and a Static IP. By allowlisting the Static IP to mission critical SaaS applications, MSPs and clients can lock access to tools, and minimize their attack surface.
Businesses should immediately update their ScreenConnect to the patched version, conduct a thorough security audit to check for signs of compromise, and apply multi-factor authentication and other security best practices. Engaging with a cybersecurity solution like Timus can also bolster their defenses against future attacks.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.
