What is Zero Trust Network Security?
In an era where digital transformation shapes every facet of business operations, and hybrid work became the norm, securing corporate networks against ever-evolving threats has become a paramount concern. At Timus Networks, we advocate for a network security approach that is based on the fundamentals of Zero Trust paradigm. This blog demystifies Zero Trust Network Security, […]
Author
Date
Category
All Categories
- AI-powered security
- Attacks & Threats
- Cybersecurity
- Hybrid Cloud
- Network
- Network Firewall
- Network Protection
- News
- Remote Workforce
- Security
- Zero Trust
Contents
Popular Posts
Product
Join the Newsletter

In an era where digital transformation shapes every facet of business operations, and hybrid work became the norm, securing corporate networks against ever-evolving threats has become a paramount concern. At Timus Networks, we advocate for a network security approach that is based on the fundamentals of Zero Trust paradigm. This blog demystifies Zero Trust Network Security, a key building block of the Timus SASE Solution, offering insights into its mechanisms, benefits, and practical applications.
Identifying the Gaps: Traditional Security Models
Traditional network security models operate on an outdated principle: trust but verify. Once inside the network, users and devices are generally trusted by default, exposing businesses to internal threats and lateral movement of attackers. This inherent trust creates significant security gaps, as it fails to consider the sophisticated nature of modern cyber threats that often breach perimeter defenses.
Zero Trust Principles in Depth: Beyond the Basics
Zero trust network security is predicated on the principle of “never trust, always verify.” It asserts that trust should never be implicit within the network, regardless of the source or location. Below, we delve into the core principles of zero trust network security, providing a roadmap to a more secure corporate network.
Guardians of Access: Two-Factor Authentication and Authorization
Two-factor authentication (2FA) and authorization are the initial checkpoints in a Zero Trust framework, ensuring that only verified users and devices can access network resources. 2FA adds an extra layer of security by requiring users to provide two different types of information before gaining access.
Multi-factor Authentication (MFA)
Building on 2FA, Multi-factor Authentication (MFA) introduces additional verification factors, making unauthorized access exponentially more difficult. MFA combines something the user knows (password), something the user has (security token), and something the user is (biometric verification), fortifying the authentication process.
Timus SASE Zero Trust Behavioral Policies
As good as 2FA and MFA are, they are not hacker-proof. There are many ways hackers have managed to circumvent MFA measures to get access to sensitive data, or business SaaS apps, like business email.
As part of its software-defined security perimeter by its Cloud Firewall, the Timus SASE Solution provides the richest set of behavior-driven conditional access policies in the market today before it authorizes access to the network, SaaS apps or other company resources.
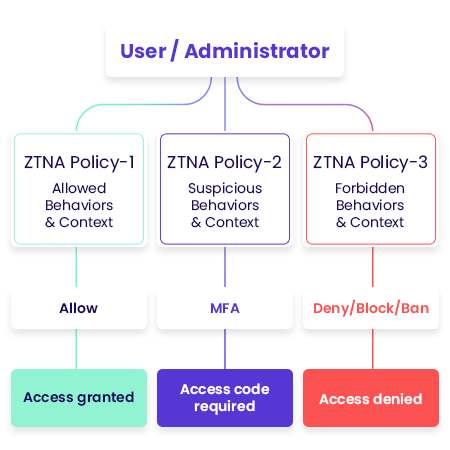
Some of the behaviors that are checked as part of the Timus zero trust network access policies are location, new device, untrusted IP, email breach in the dark web, impossible travel made, and more. Only when a risk threshold is reached, an adaptive MFA is sent out to reduce any user MFA fatigue.
Ciphering the Secrets: Navigating Encryption and Data Integrity
Encryption and data integrity checks are crucial for safeguarding data in transit and at rest. By encrypting data, Zero Trust security ensures that even if data is intercepted, it remains undecipherable to unauthorized entities. Data integrity mechanisms prevent tampering, maintaining the authenticity of information.
The OS-agnostic Timus agent on the user devices (laptops, and mobile devices) uses AES-256 encryption to encrypt any user traffic between the end-device and the Timus Cloud Firewall. The dedicated Timus cloud firewall sits between the access requests and the corporate network, acting as the single point of entry to the resources.
Network Fortification: Zero Trust Networks
At the heart of Zero Trust is the concept of least privilege access and microsegmentation. Least privilege access ensures that users have access to only what they are authorized to do their job; microsegmentation divides the network into smaller, isolated segments. The principle of least privilege and microsegmentation limit lateral movement and minimizes the attack surface by applying strict access controls to each segment.
Microsegmentation
Microsegmentation takes network segmentation further, applying granular security policies at a much finer level. It not only isolates environments from one another but also controls traffic flow between individuals or groups of resources, enhancing security within the network.
What are the Benefits of Zero Trust?
Zero Trust Network Security offers a myriad of benefits, from enhanced security posture and reduced attack surface to improved compliance with regulations and data protection. By enforcing strict access controls and continuous verification, Zero Trust minimizes the risk of internal and external breaches, ensuring that only authenticated and authorized entities can access sensitive resources.
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) extends the Zero Trust principles to network access, ensuring that users and devices are authenticated and authorized before being granted access to network applications. ZTNA solutions, such as Timus SASE, provide secure, context-aware access to corporate resources, enhancing flexibility and security for remote and hybrid workforces. The Timus ZTNA solution provides secure, always-on connectivity for remote users regardless of the location or device they’re accessing the network from.
Cloud Harmony: Integrating Zero Trust Security with Cloud Services
As businesses increasingly migrate to the cloud, integrating Zero Trust security becomes essential. Zero Trust principles can be applied to cloud environments, ensuring Secure Access to cloud services and applications.
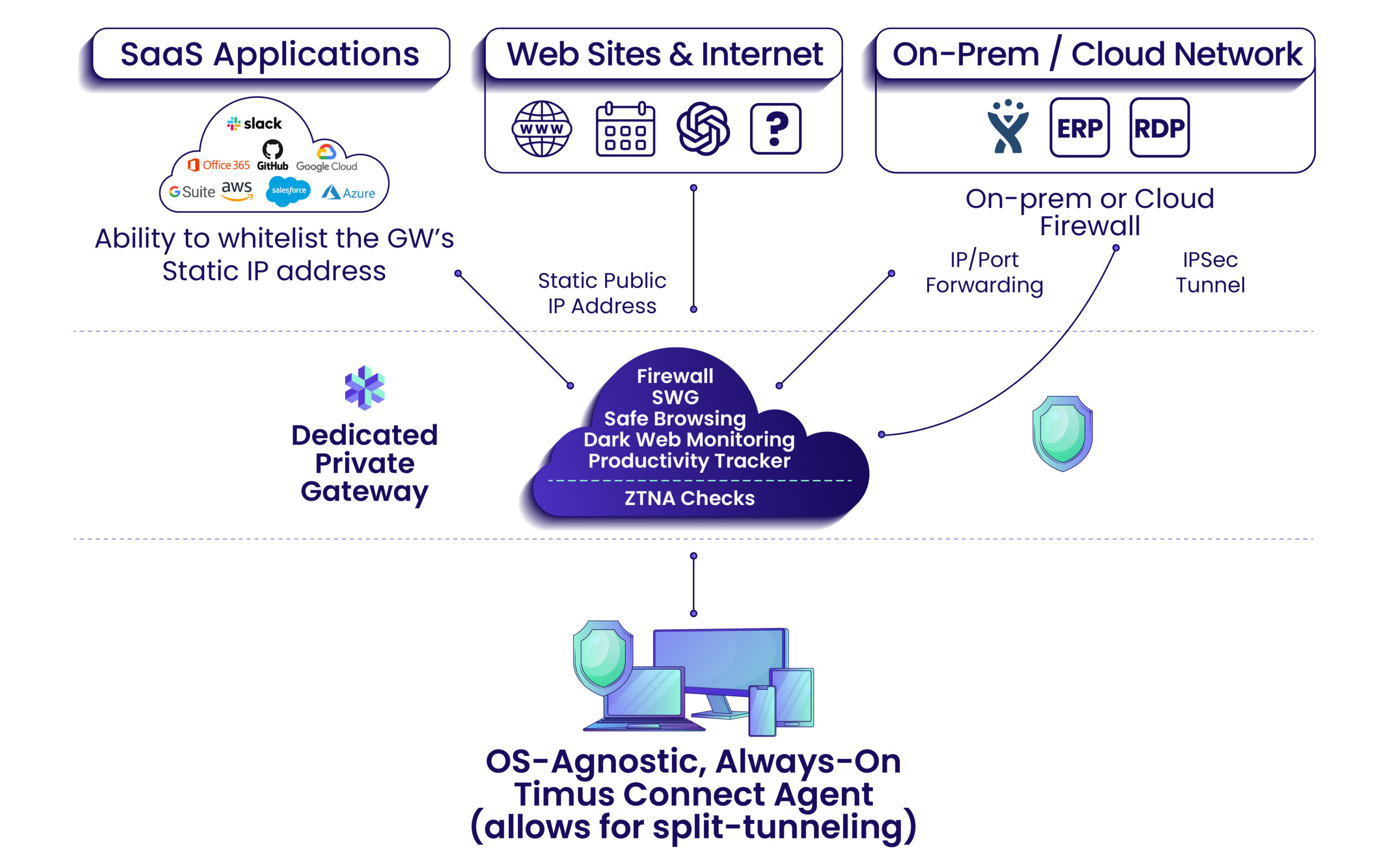
The Timus Adaptive Cloud Firewall, a key part of the Timus dedicated client gateway, is ideally suited for companies that have hybrid cloud networks, or have moved all their resources to the cloud. It sits between the endpoints and a company’s resources, whether they’re in the cloud or on-prem, and intercepts all traffic via one central location. The Security buffer and single entry point to the network, the software defined perimeter is controlled from a single cloud managed dashboard.
Zero Trust Security and Business SaaS Applications
One of the top three reasons for a small to medium business to suffer significant monetary loss is business email compromise. With advanced social engineering tactics, it is becoming increasingly prudent to protect a business’ SaaS applications from breaches. In today’s world through various tactics, it is commonplace to find a user’s SaaS credentials on the dark web. As a lot of users use the same password for both personal and business apps, hackers utilize credential stuffing to breach into corporate applications. Thus zero-trust network security deployments where a user’s identity is thoroughly verified via contextual policies becomes critical.
The Timus SASE solution does not stop here however. In addition to having the richest set of ZTNA policies in the market, Timus also provides a static dedicated IP address to control access to the network via allowlisting the static IP address. Even if the hacker stole the credentials, he or she would not be able to get access as the IP address would not be part of the allowlist.
Leveraging a dedicated static IP address offers maximum network control.
Navigating the Implementation Maze: Talk to Timus Networks Today
In today’s risk economy, a business can achieve the much desired “peace of mind” by implementing zero trust network security as part of its layered security approach to help minimize the network attack surface. Zero trust policies also help make it easier to achieve compliance in some of the regulated industries.
Timus Networks prides itself for having one of the richest set of zero trust access policies while making its platform easy to use and easy to deploy, usually in less than an hour.
By understanding and implementing the zero trust network access principles, organizations can significantly enhance their security posture, protect against sophisticated cyber threats, and adapt to the ever-changing digital landscape. At Timus Networks, we are committed to guiding businesses through this transformative journey, ensuring a secure and resilient future. Contact us today for a demo.
FAQ
Zero Trust Network Access (ZTNA) is based on the “never trust, always verify” principle, implying that trust is never granted before completely verifying. Access is granted granularly on the least privilege principle, where a user can only access explicitly authorized resources and data. ZTNA is one of the core components to providing secure, always-on connectivity to remote users, or users who are accessing SaaS apps on company devices.
Like all cybersecurity solutions, you don’t need them until you do and then it’s too late. ZTNA helps protect your network against ransomware and other nefarious attacks. One of the biggest weaknesses in modern cybersecurity defenses is the human element. If access to your network relies on credentials alone, you’re only one human error away from getting your data hacked or worse. The Timus ZTNA helps prevent access to precious company resources from unwanted third parties.
There are several disadvantages to VPNs that Timus solves by eliminating them with ZTNA. 1. Traditional VPNs are clunky 2. They are not always-on 3. VPN credentials are easily stolen by social engineering and phishing 4. A hacker can move laterally within the network via stolen VPN credentials. Timus ZTNA allows users to access company resources in a granular way with secure, always-on connectivity through a lightweight OS-agnostic agent.
Zero Trust and Least Privilege are two foundational principles in cybersecurity, each addressing security control from slightly different perspectives. Zero Trust is a security model that operates on the premise that no entity, either inside or outside the network, should be automatically trusted. This model requires continuous verification of the legitimacy of all access requests, regardless of their origin, before granting access to resources. Least Privilege, on the other hand, is a principle that dictates that users, systems, or processes should only have the minimum level of access necessary to perform their functions. This reduces the risk of an attacker gaining access to critical systems or data through a less secure part of the network. While Zero Trust encompasses a broader strategy including technologies and policies for securing the organization’s assets, Least Privilege is more specifically focused on the appropriate allocation of access rights within the system or network. Both principles aim to minimize risk by reducing the attack surface.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.
