Understanding the TunnelVision Vulnerability
On May 6, 2024, Leviathan Security Group (LVG) identified a new hacking technique named TunnelVision. It allows attackers to bypass VPN encapsulation and send traffic outside a VPN tunnel using Dynamic Host Configuration Protocol (DHCP). The LVG reported TunnelVision to the Cybersecurity and Infrastructure Security Agency (CISA), which quickly flagged the vulnerability as a high-priority […]
Author
Date
Category
All Categories
- AI-powered security
- Attacks & Threats
- Cybersecurity
- Hybrid Cloud
- Network
- Network Firewall
- Network Protection
- News
- Remote Workforce
- Security
- Zero Trust
Contents
Popular Posts
Product
Join the Newsletter

On May 6, 2024, Leviathan Security Group (LVG) identified a new hacking technique named TunnelVision. It allows attackers to bypass VPN encapsulation and send traffic outside a VPN tunnel using Dynamic Host Configuration Protocol (DHCP). The LVG reported TunnelVision to the Cybersecurity and Infrastructure Security Agency (CISA), which quickly flagged the vulnerability as a high-priority threat, emphasizing the importance of immediate mitigation. This critical vulnerability has been assigned CVE-2024-3661, and software vendors whose products were affected released patches and guidelines for securing networks against TunnelVision. This blog aims to provide an in-depth understanding of TunnelVision, its operation, and recommendations to protect your network.
How It Works
TunnelVision involves routing traffic without encryption through a VPN using the attacker’s configured DHCP server using option 121. Defined in RFC 3442 as the “Classless Route Option,” option 121 allows a DHCP server to supply additional static routes in addition to the default gateway route. The DHCP server can then redirect the traffic to the Internet via a side channel created by the attacker. The VPN never encrypts the packets on that side channel. Hence, an attacker can snoop on their traffic. The existing VPN tunnel remains intact, and the VPN client still believes it’s communicating with the corporate network securely, while the traffic would actually go through a malicious server. This attack allows hackers to reroute traffic to their servers, capturing sensitive data.
According to Leviathan Security Group, the vulnerability also “allows for arbitrary code execution” through the VPN software by manipulating “scripts executed on VPN connection or disconnection,” ultimately granting attackers complete control over the system.
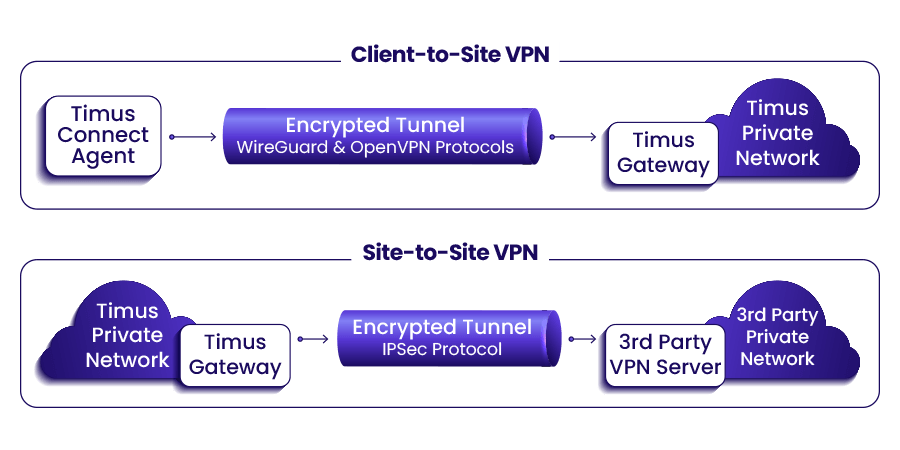
Does TunnelVision (CVE-2024-3661) impact Timus Networks?
VPN-based security solutions that rely on DHCP and routes to redirect traffic are vulnerable to TunnelVision. Timus Networks does not use the described technique above to create encrypted tunnels between the endpoint agents and dedicated client gateways. As such, Timus Gateways are not exposed to the TunnelVision technique.
How to Protect Your Network from TunnelVision
- Patch Management: Ensure that all security appliances are updated with the latest patches addressing CVE-2024-3661.
- Zero Trust Network Architecture: Adopt a Zero Trust model that verifies each access request regardless of location.
- VPN Hardening:
Use multi-factor authentication (MFA) for all VPN connections.
- Limit VPN access to authorized personnel only.
- Regularly review and remove inactive VPN accounts.
- Apply strict network policies to VPN client software.
- Network Segmentation: Isolate critical systems and minimize lateral movement by segmenting your network.
- Monitoring and Detection:
- Deploy an Intrusion Detection System (IDS) to monitor VPN traffic.
- Regularly review logs for abnormal connection patterns.
- Security Awareness Training: Educate employees about phishing attacks and social engineering tactics.
Recommendations
- Immediate Action: Apply the latest patches from vendors and harden your VPN configurations.
- Review Network Architecture: Consider adopting Zero Trust principles and segmenting your network to reduce the attack surface.
- Regular Security Audits: Conduct periodic security assessments to identify and fix configuration flaws and outdated practices.
- Continuous Monitoring: Implement real-time monitoring to quickly detect and respond to anomalous activities.
Conclusion
TunnelVision (CVE-2024-3661) serves as a wake-up call for organizations relying heavily on VPN tunnels. By adopting a proactive security posture and implementing the recommended measures, organizations can significantly reduce their exposure to this vulnerability. Stay vigilant, stay updated, and ensure your network remains secure.
Need help securing your network? Timus Networks offers a comprehensive Zero Trust Architecture-based SASE solution tailored to MSPs, MSSPs, and their clients’ network security needs. Contact us today to learn more.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.
