Network Segmentation: What Does it Entail and Why is it Crucial?
What is Network Segmentation? Network segmentation refers to the subdivision of a computer network into smaller parts, each acting as an autonomous micro-network. This approach provides network administrators with granular control over network traffic flowing across different subnets, guided by tailored policies. This process is pivotal in enhancing monitoring capabilities, bolstering performance, localizing technical problems, […]
Author
Date
Category
All Categories
- AI-powered security
- Attacks & Threats
- Cybersecurity
- Hybrid Cloud
- Network
- Network Firewall
- Network Protection
- News
- Remote Workforce
- Security
- Zero Trust
Contents
Popular Posts
Product
Join the Newsletter

What is Network Segmentation?
Network segmentation refers to the subdivision of a computer network into smaller parts, each acting as an autonomous micro-network. This approach provides network administrators with granular control over network traffic flowing across different subnets, guided by tailored policies. This process is pivotal in enhancing monitoring capabilities, bolstering performance, localizing technical problems, and crucially, fortifying security.
By implementing network segmentation, organizations can effectively safeguard their highly valuable assets, such as customer data, corporate financial records, and intellectual property. These assets often reside in hybrid and multi-cloud environments that span public clouds, private clouds, and software-defined networks (SDNs), all of which necessitate robust security measures to guard against cyber attacks and data breaches.
What Are the Fundamental Principles Behind Network Segmentation?
The principle of network segmentation revolves around the concept of trust in network security. In earlier times, network architects aimed their security strategies at the internal network perimeter, an invisible boundary separating the external world from the enterprise’s vital data.
Individuals within this perimeter were presumed to be trustworthy and thus not a threat. Consequently, they faced minimal restrictions on their access to information. However, this trust assumption has been challenged with the evolution of cyber threats, prompting organizations to adopt a more cautious approach, known as Zero Trust.
How Does Network Segmentation Work?
Network segmentation operates on the Zero Trust strategy, which assumes that no entity is inherently trustworthy, even those already within the network perimeter. This strategy is based on the principle of a ‘protect surface’ built around the organization’s most critical data, applications, assets, or services (DAAS).
Network segmentation comes into play by allowing architects to construct a micro-perimeter around the protect surface, effectively forming a second line of defense. By doing so, authorized users gain access to assets within the protect surface, while all others are barred by default.
What are the Benefits of Network Segmentation?
Network segmentation brings several key benefits to the table:
- Stronger Network Security: Segmentation splits the network into smaller subnetworks, limiting the attack surface and obstructing lateral movement. It also isolates attacks before they can proliferate, ensuring a localized impact.
- Less Network Congestion and Better Performance: Network segmentation significantly reduces congestion. In the case of a network with an overwhelming number of network hosts, congestion can occur due to excessive packet transmission, impacting performance. Subnetting, or breaking the network into smaller segments, effectively alleviates congestion.
- Decreased Scope of Compliance: Regulatory compliance costs can be curtailed through network segmentation, as it reduces the amount of in-scope systems.
How Does Network Segmentation Improve Security and Reduce Risks?
Network segmentation is a proactive defense strategy that seeks to address potential risks and vulnerabilities before they can be exploited. By dividing the network into smaller sections, network segmentation can limit the potential scope of a security breach.
This is achieved by keeping threats isolated within a particular segment, preventing lateral movement that could expose the entire network to the threat. This approach is particularly effective in minimizing the attack surface, thereby reducing the risk of data breaches and enhancing network security.
Which Methods and Tools Are Used to Put Network Segmentation Into Practice?
Network segmentation can be implemented through physical or logical segmentation.
Physical segmentation involves the breakdown of a larger computer network into a collection of smaller subnets, with a physical or virtual Firewall acting as the subnet gateway, controlling inbound and outbound traffic. The advantage of physical segmentation lies in its straightforward administration due to the fixed topology.
On the other hand, logical segmentation creates subnets using virtual local area networks (VLANs) or network addressing schemes. VLAN-based approaches are relatively easy to implement as the VLAN tags automatically route traffic to the appropriate subnet. Network addressing schemes, while equally effective, require a more detailed understanding of networking theory.
What Challenges Are Encountered When Deploying Network Segmentation Solutions?
While network segmentation offers numerous benefits, it also presents certain challenges. One of the primary challenges is managing and maintaining the segmentation as the network grows. Adding more devices or users to the network could necessitate the creation of additional segments, or an upgrade to existing ones, leading to increased costs and complexity.
Another challenge is ensuring that the segmentation does not adversely affect network performance. Excessive segmentation can lead to increased congestion and reduced network speeds. This necessitates careful planning and monitoring to balance security needs with performance requirements.
How Can Businesses Plan and Implement Network Segmentation Strategies Effectively?
The successful planning and implementation of network segmentation strategies require a thorough understanding of the network and its components. Businesses should start by conducting a comprehensive network audit to identify all devices, applications, and data flows within the network.
Next, businesses should develop a detailed network segmentation plan that outlines the desired segments, their respective security policies, and the process for implementing the segmentation. This plan should also include provisions for ongoing monitoring and management of the segmented network.
Finally, businesses should leverage the right tools and technologies to implement the network segmentation. These could include firewalls, virtual local area networks (VLANs), and network access control (NAC) solutions.
What Part Does Network Segmentation Play in Regulation and Compliance?
Network segmentation plays a crucial role in helping organizations comply with various data protection and security regulations. By isolating sensitive data within specific network segments, businesses can better protect this data and demonstrate compliance with regulations such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR).
By restricting access to sensitive data to only those who need it, network segmentation helps enforce the principle of least privilege, a core requirement of many regulatory standards. Furthermore, the enhanced visibility and control offered by network segmentation can aid in demonstrating compliance during audits.
What is Network Segmentation Best Practices?
To maximize the benefits of network segmentation, businesses should adhere to several best practices:
- Limit Over-segmentation: Over-segmentation can decrease overall network visibility and make management difficult. Balancing the number of segments with the need for security is key.
- Perform Regular Audits: Continual audits of the network segments for vulnerabilities, tight permissions, and updates ensure that the network remains secure.
- Follow the Principle of Least Privilege: Applying the principle of least privilege across all segments ensures that users only have the level of access they need to perform their jobs.
- Limit Third-Party Access: Granting third parties access to the network should only be done where necessary and with strict controls in place.
- Automate Where Possible: Automation can simplify the configuration and management of network segments, reducing the risk of human error.
Where in a Network Segment Will the DMZ be Located?
The Demilitarized Zone (DMZ), a physical or logical subnetwork that exposes an organization’s external-facing services to the internet, is typically located in a separate network segment. This arrangement provides an additional layer of security, as it isolates the DMZ from the internal network.
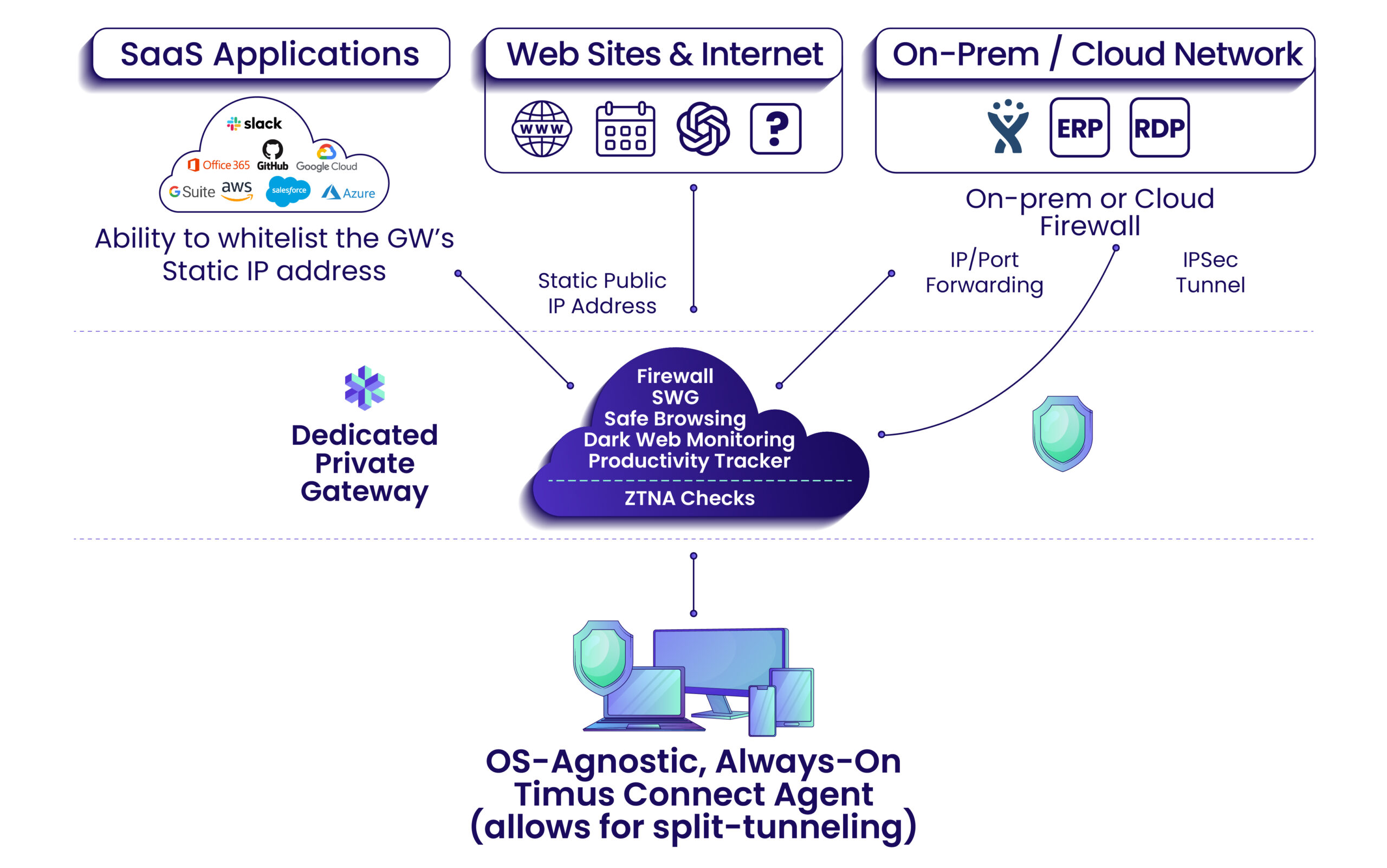
Which Choice is a Good Reason to Segment a Network?
Implementing Timus Zero Trust Network Access (ZTNA) with micro-segmentation capabilities is a good reason to segment a network. Timus ZTNA enables the implementation of least privilege access control via Timus with granular access policies. This allows organizations to create micro-segmented networks, where access is tightly controlled based on specific criteria such as user identity, Device Posture, and contextual factors. By employing micro-segmentation, businesses can significantly reduce the attack surface, prevent lateral movement of threats, enhance network performance, and meet regulatory compliance requirements. Timus ZTNA provides a robust framework for implementing effective network segmentation strategies, thereby bolstering overall security posture.
FAQ
An example of a network segment could be a subnet dedicated to a specific department within an organization, such as the finance or HR department. Each departmental subnet could have its own security policies and access controls, tailored to the specific needs and risks associated with that department.
Yes, a Virtual Local Area Network (VLAN) is a form of logical network segmentation. It allows network administrators to partition a physical network into multiple broadcast domains, each of which can be secured and managed independently.
While both are methods of dividing a network, a network segment refers to a subdivision of the network, often based on physical or logical boundaries. A zone, on the other hand, typically refers to a logical area within a network where specific security policies are enforced.
While both involve dividing a network into smaller parts, network segmentation typically refers to the division of the network into separate segments or subnets. Network segregation, on the other hand, usually refers to the isolation of different types of network traffic to prevent them from interacting with each other.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.
