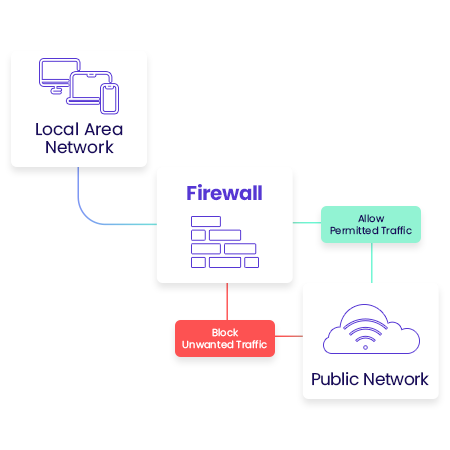
Adaptive Cloud Firewall
The Timus firewall sits in the cloud and intercepts all encrypted user traffic. Admins can create granular user based policies to restrict network access to the specific needs of the business.
30 days free with a Satisfaction Guarantee
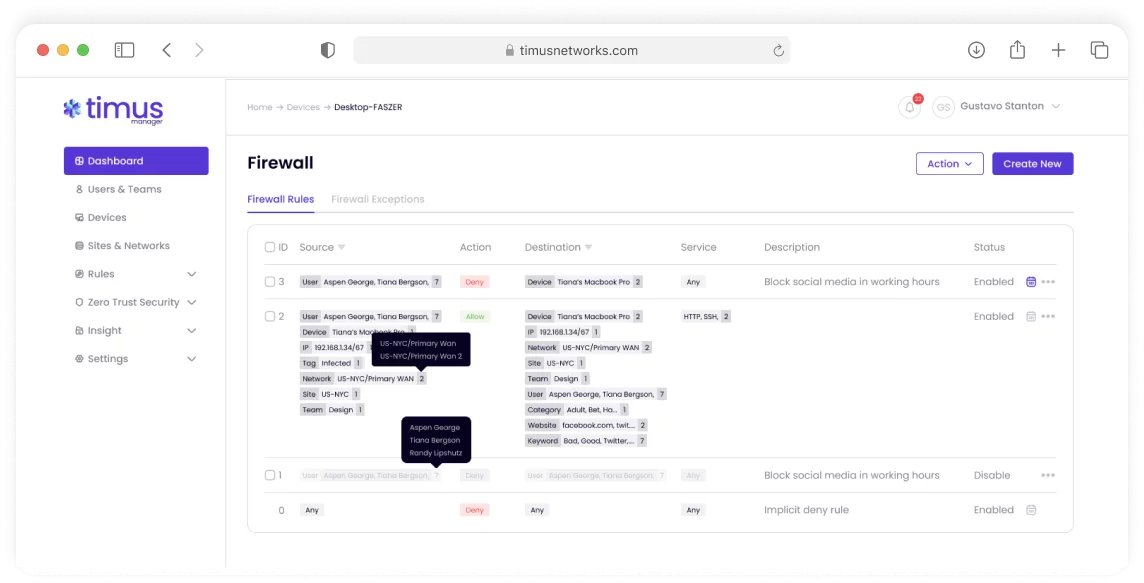
Software-Defined Security Perimeter
Dynamic Firewall Follows Users in Real-Time
SW-defined security perimeter expands and contracts with the user. Rules follow users and devices on all gateways.
Identity is the New Perimeter
Rules are input based on identity and context, ensuring zero-trust access, and proper routing of users to sensitive data along with blocking malicious activities.
Single-point of Network Entry
Timus Cloud Firewall acts as a single-point of entry to all corporate resources, whether on-premise or in the cloud. Timus stops bad actors at the front door via global user sign-in policies.
Granular Security Based on User
Layer-3 and Layer-7 stateful firewall as a service. Granular rules take effect in seconds.
Operational Efficiency
Set global policies within the Timus admin interface built with IT admins in mind. Reduction in clicks for the admin without compromising security.
Custom, Automated Reports
Custom automated reports providing valuable insights into user activity with intervals of daily, weekly, monthly or yearly. Actionable event logging leading to quicker ticket resolution
Layering Protection
Users will be users. Bad actors will be bad actors. Layering protection from the inevitable credential leak mitigates fallout. Timus restricts access beyond traditional MFA.
Redundancy
The Timus global infrastructure backbone ensures uptime and high availability. 48 Global points of presence. Intelligent connection routes users through the fastest tunnel.
Get Started In Minutes
Get started in minutes with deployments under an hour. Timus adapts with new additions, users & connection points.
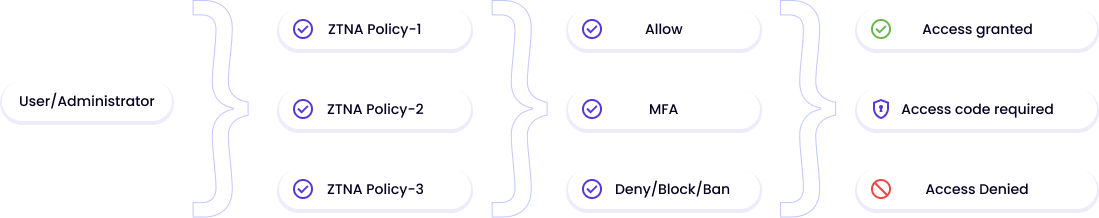
Scalable
The Timus solution is delivered fully cloud-based. Fitting seamlessly with existing infrastructure without complicating future enhancements.
Interconnected
Cloud Firewall connects via IPsec tunnels to AWS, Azure, GCP & All on-premise firewalls. Secure SaaS apps with IP allowlisting the gateway’s dedicated IP address.
FAQ
An adaptive cloud firewall sets the (SW-defined) security perimeter to wherever the users might be accessing the data from. It can assess risk on a user’s access request based on not only credentials, but also user behavior and the context of the request. In addition, it reduces MFA fatigue by enforcing MFA only when the threshold on the risk profile is exceeded. It also scales and adapts with each new user or endpoint additions.
Timus does not replace an existing on-prem firewall; rather it acts as a single point of entry to all company networks and resources, creating a security buffer. Once the user is thoroughly verified via the ZTNA checklist, he or she can then be orchestrated to their destination via IPSec tunnels including to on-prem firewalls. For clients with no offices, the Timus cloud firewall can replace the need for any other additional FW.
Combining a cloud firewall with an on-prem appliance creates a layered security approach. This defense-in-depth strategy offers scalability, redundancy, granular control, and compliance adherence. It’s particularly valuable in hybrid cloud environments ensuring comprehensive protection, geographic redundancy, and centralized logging for effective network security management.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.