×
Limited Time Offer! Get 40% Discount on Timus SASE Advanced Plan. Learn More
Adopting a strong security strategy is crucial in the current digital environment, where cyber threats abound. The conventional castle-and-moat method, which relied on the trust of everything within the network perimeter, is becoming outdated. The zero-trust security model, however, represents a significant shift. It questions the idea of inherent trust and ensures that every user, device, and…
Author
Date
Category
All Categories
Contents
Popular Posts
Product

Adopting a strong security strategy is crucial in the current digital environment, where cyber threats abound. The conventional castle-and-moat method, which relied on the trust of everything within the network perimeter, is becoming outdated. The zero-trust security model, however, represents a significant shift. It questions the idea of inherent trust and ensures that every user, device, and application undergo continuous verification before being granted access to sensitive resources.
This guide explores the complexities of implementing a zero-trust architecture, equipping you with the knowledge and best practices to fortify your organization’s defenses against ever-evolving cyber threats.
Zero-trust implementation refers to the process of adopting a security framework that operates on the principle of “never trust, always verify.” This approach mandates that every access request, regardless of its origin – internal or external – is subjected to stringent authentication, authorization, and continuous monitoring measures.
The fundamental principle of zero-trust is to remove the idea of a trusted network boundary, acknowledging that threats can arise from within and outside the organization. zero-trust implementation seeks to reduce the attack surface and lessen the impact of successful breaches by considering every user, device, and application as a potential threat.
Transitioning to a zero-trust security model is a multifaceted endeavor that requires careful planning, execution, and ongoing monitoring. Here are five essential steps to guide you through the implementation process:
Secure Access Service Edge (SASE) is a cloud-native security architecture that converges networking and security functionalities into a unified, globally distributed service. Implementing SASE as part of your zero-trust strategy can provide several benefits, including:
Micro-segmentation involves dividing your network into smaller, isolated segments based on specific security requirements. By implementing micro-segmentation, you can define granular access controls, allowing users, applications, and devices to access only the resources they require to perform their designated tasks.
This approach significantly reduces the attack surface and limits the potential for lateral movement within your network, effectively containing threats and minimizing the risk of widespread data breaches.
Multi-factor authentication (MFA) is a foundational element of zero-trust security. It mandates that users furnish two or more authentication factors, including something they know (e.g., a password), something they possess (e.g., a mobile device or token), and something they are (e.g., biometric data like fingerprints or facial recognition).
By implementing MFA, you can significantly enhance the security of your systems by ensuring that only authorized users with valid credentials can gain access, reducing the risk of unauthorized access and account compromises.
The principle of least privilege (PoLP) is a fundamental concept in zero-trust security. It dictates that users, applications, and devices should be granted only the minimum level of access required to perform their specific tasks or functions.
By adhering to the PoLP, you can minimize the potential impact of successful breaches and limit the ability of malicious actors to move laterally within your network, effectively containing threats and reducing the risk of data exfiltration or system compromise.
In a zero-trust environment, endpoint devices are considered potential entry points for threats. As such, it is crucial to implement robust endpoint security measures, including device validation, encryption, and continuous monitoring.
Ensure that all endpoint devices meet your organization’s security requirements before granting them access to your network resources. This may involve device enrollment, software and firmware updates, and the deployment of endpoint protection solutions.
While the benefits of a zero-trust security model are undeniable, its implementation can be demanding on resources and organizations must be prepared to address this.
Achieving a strong zero-trust security posture requires a systematic approach that includes several essential elements:
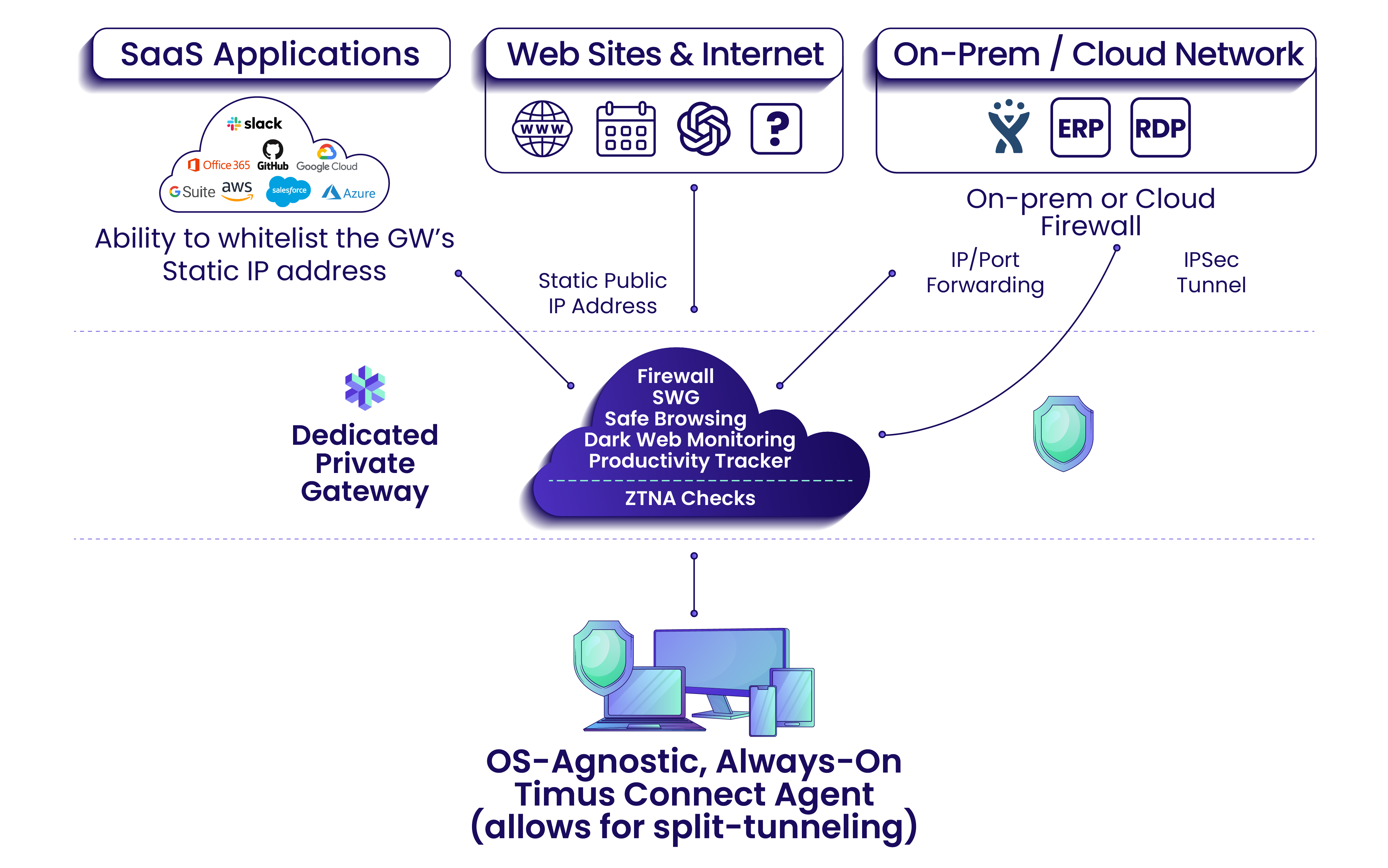
Timus provides an acclaimed Zero Trust Network Access (ZTNA) solution that employs a comprehensive behavioral context checklist to verify users before granting access. This includes identity-based verification, Adaptive MFA, and intelligent threat detection through an adaptive cloud firewall. By eliminating the need for VPNs, Timus ZTNA offers continuously secure connectivity.
Core Principles of ZTNA
Advantages of ZTNA Over Traditional VPNs
Disadvantages of Traditional VPNs
Timus ZTNA addresses several drawbacks of traditional VPNs, including:
Timus ZTNA offers granular access to company resources with secure, always-on connectivity through a lightweight OS-agnostic agent.
While there is no one-size-fits-all approach to zero-trust security, several best practices can guide organizations in their implementation efforts:
Implementing zero-trust can be demanding, particularly for organizations with complex infrastructures and legacy systems. However, by adopting a phased approach, engaging stakeholders, and leveraging expert guidance, you can mitigate the challenges, and the benefits of enhanced security and reduced risk can outweigh the initial effort.
Firewalls can still play a role in certain implementations. However, zero-trust extends beyond firewalls by incorporating additional layers of security, such as micro-segmentation, identity and access management, and continuous monitoring.
The time required to implement zero-trust varies depending on your organization’s complexity, the solution chosen, and the scope of your implementation. Larger organizations with intricate infrastructures may need more time to document processes, define access controls, and segment their networks. However, investing time upfront to assess and plan for your critical assets can streamline the process. By embracing the zero-trust security model, organizations can fortify their defenses against modern cyber threats, protect their sensitive data and critical assets, and foster a culture of continuous vigilance and trust-based access. While the journey may present challenges, enhanced security, reduced risk, and a resilient security posture make the effort worthwhile in today’s ever-evolving threat landscape.
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.