Get Compliant with Timus
Timus Networks uses AES-256 encryption, and is SOC 2 Type 2 and ISO 27001 compliant.
Partner with Timus to ensure your security meets the highest standards.

Leverage Timus to Achieve and Maintain Compliance
Comprehensive Suite of Features
Timus provides a suite of features to enhance security of data and information, including asset management, vulnerability identification, access control, incident response, and risk assessment.
Check all the boxes with Timus
Incorporating Timus into an organization’s security infrastructure strengthens its security posture, promotes transparency, provides deep network visibility, and ensures compliance.
Security & Privacy
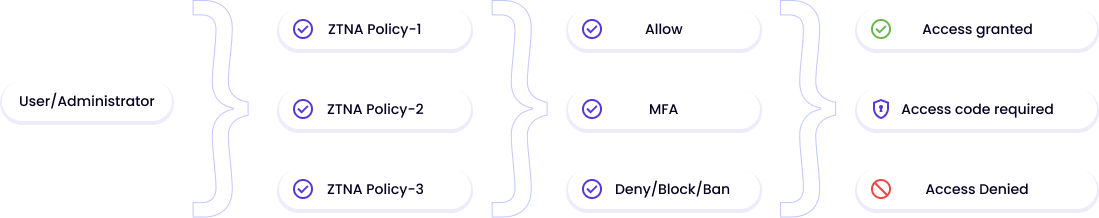
Timus’ zero trust network security approach and dynamic cloud firewall both deliver the highest level of security so your network, data, and applications are kept safe and private.
Availability
The network embedded nature of Timus combined with the granular traffic and access logs, ensures insights and data are readily available in case of an incident.
Processing Integrity & Confidentiality
All data processed within the software-defined perimeter set by Timus is protected and safe from unauthorized access whether internal or external.
Deep Network Visibility
With the always-on Timus Connect agent on devices, and the cloud firewall as the single point of network entry, IT administrators have 100% visibility into the activities on the network with no blind spots.
Built for the Service Provider
Timus is built with the IT administrators in mind. Our mission of keeping users connected and protected, while ensuring clients remain compliant with regulations, is achieved with ease of deployment and straightforward management.
Leverage Compliance Features
Get access to a suite of features that align with SOC 2 Type 2 and ISO 27001 compliance requirements.
Manage Data, Traffic, and Access
Efficiently manage your assets, enforce control measures, and regulate access, ensuring you maintain complete control at all times.
Establish a Stronger Security Posture
Identify vulnerabilities, analyze threats, remediate issues, and mitigate incidents before they escalate.
Handle Supply Chain Risks
Evaluate third-party vendor and business partner risks and respond effortlessly to data controller requests.
Learn how Timus helps you stay secure and compliant.
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.

