Detect Threats at the
Network Level
Timus Secure Web Gateway (SWG) enables safe browsing for employees by blocking malware and phishing at the network level.
30 days free with a Satisfaction Guarantee
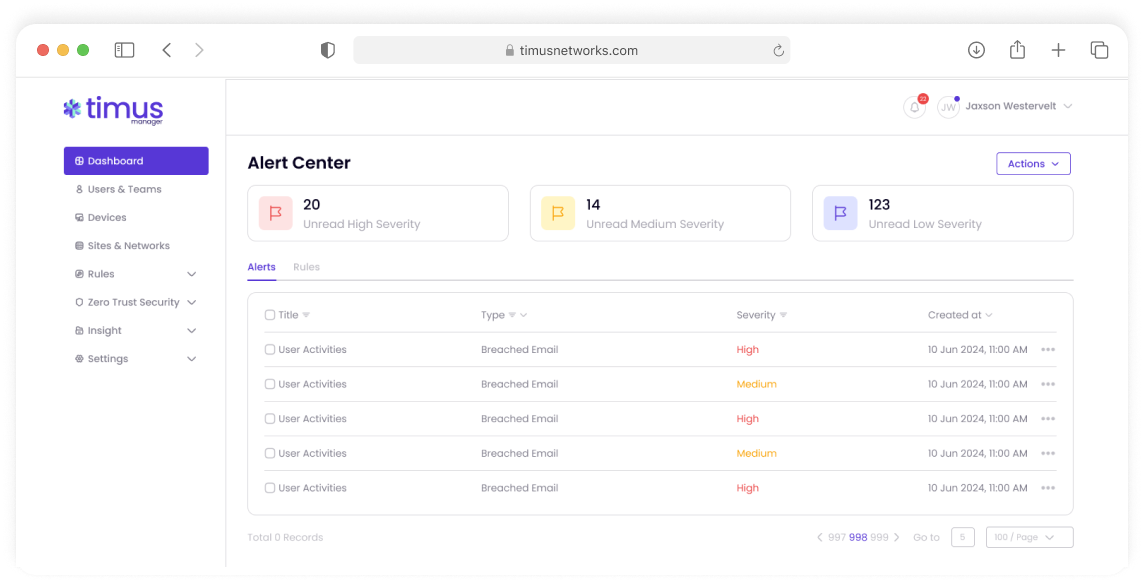
SWG Part of Cloud Firewall
Safe Browsing
With network-level antivirus protection and URL-based web filtering, Timus provides a safe environment to browse the internet. Phishing and malicious sites blocked before they can do damage.
Secure Web Gateway
Protect employee web usage with category filtering and prevent access to unwanted and unsafe sites. Ability to write rules for web categories, keywords, and specific websites. 30 predefined web categories.
Minimize Attack Surface
Protecting employees from malware, phishing, and malicious sites from wherever they may encounter it helps with reducing the attack surface available to bad actors.
Dark Web Monitoring
To further prevent threats, all user and system administrator email addresses are checked in the dark web every 12 hours to see if they have been a part of a breach or disclosure.
Next-Gen Network Security
By combining secure, zero-trust network access with an intelligent cloud firewall and secure web gateway, Timus provides a robust network security solution that effectively helps secure resources.
Comprehensive Full SSL/TLS Inspection with Timus SASE
Timus SASE’s SWG allows for full SSL/TLS traffic inspection to scan for malicious content within the encrypted HTTPS traffic.
Device Isolation within the Network
Through its integration with leading endpoint protection platforms on device, and the dynamic tagging feature, Timus SASE further prevents threats by isolating infected devices in the network in real-time.
Prevent Phishing
Malware and phishing are prevented from sites including drop servers, command and control botnet hosts, parked sites and domains, in addition to the fraudulent phishing sites that aim to trick users.
Stay Secure and Compliant
By blocking content from regulated categories, companies can stay compliant with business rules and regulations. Ability to customize.
Detailed Logs at the User Level
Detailed web access logs at the user level helps with productivity tracking and compliance.
Connect From Anywhere
Always-on, secure connectivity where users are automatically protected from threats.
FAQ
Hackers deploy a plethora of different tactics. Two of the most common ones are phishing and social engineering with the end goal of stealing a user’s credentials, or other sensitive information such as social security numbers or credit card numbers. Some other tactics include sneaking in malware or ransomware into attachments or websites, denial of service (DoS), or man-in-the-middle (MitM) attacks used for intercepting public Wi-Fi networks.
While not clicking on links or files that one doesn’t recognize is still very important, it is becoming more and more difficult to recognize phishing sites by the naked eye. A company must implement zero-trust-network-access policies to prevent hackers gaining access to the network via stolen/phished user credentials.
An up-to-date endpoint protection software along with regular security trainings are key. In addition, consider using a Zero Trust Network Access (ZTNA) solution. For example Timus provides secure, always-on connectivity to company resources and SaaS apps from wherever the users might be accessing them from, be it an airport, a coffee shop,
Get Started with Timus
Zero Trust. Adaptive Cloud Firewall. Secure Remote Access. In one.