Timus SASE helps MSPs modernize security by consolidating fragmented tools into a unified SASE platform. Cloud-native, fast to deploy, and built to scale.
Zero complexity. Zero downtime. Just Zero Trust.
30-day free with a satisfaction guarantee
- No Hardware
- Deployed in 30 Min
- 100% Cloud Native
The Channel-First SASE Platform MSPs Rely On
Replace legacy VPNs with always-on, zero-click access
Enforce zero trust with the richest set of contextual policy controls in the market
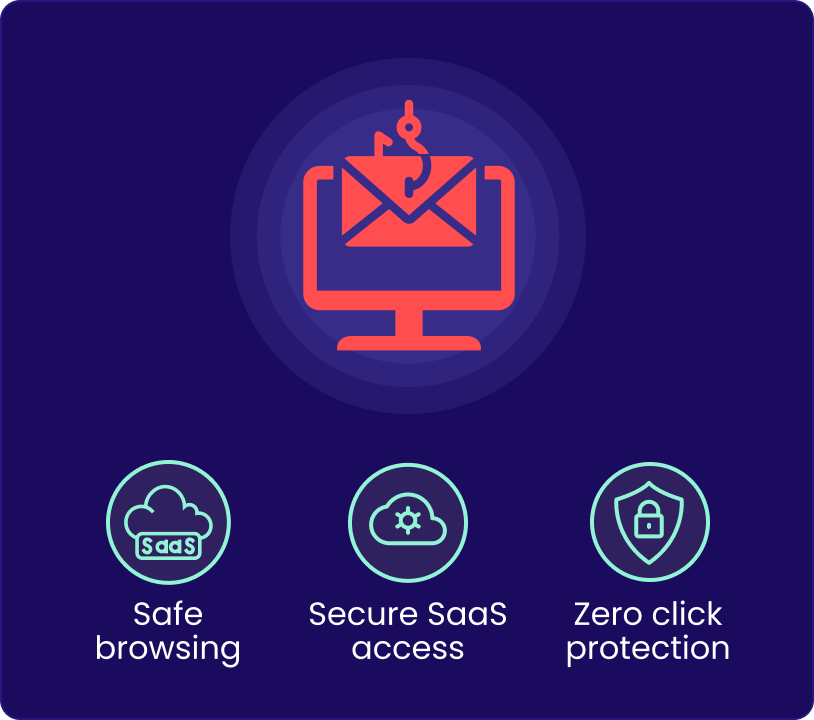
Enable phish-free browsing via cloud-based secure web gateways
Make compliance effortless by least privilege access, deep network visibility, and rich reporting
With Timus, You Are...
Starting Strong
Timus is partner-crazed. We have the best onboarding and support team amongst our competitors
Empowered to Scale
Deploy Zero Trust across clients in minutes, not months
Always Protected
Ensure continuous security with always-on SASE
Operationally Efficient
Reduce support tickets and streamline management

Ready to Accelerate Your Growth
Transform security services into a profitable offering

Seamlessly Integrated
Effortlessly layer Timus SASE into your existing MSP stack
Securing Trust, Leading the Future
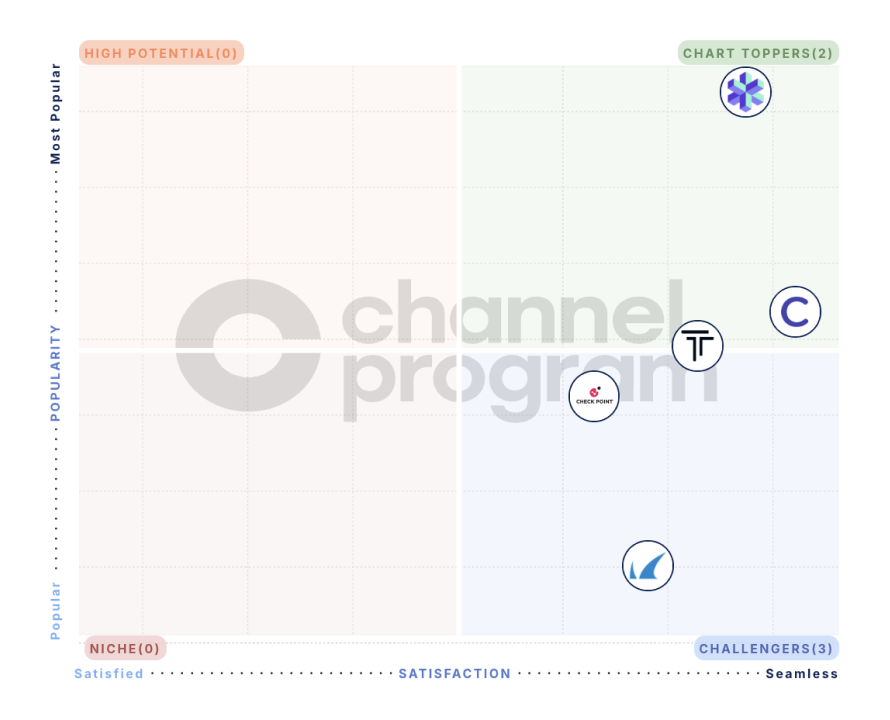
Proven Impact for Growth-Focused MSPs
The Metrics MSPs Run On
Secure Access. Actionable Insights. Complete Control.
We Fired Half Your Stack. You Won’t Miss It.
Say Goodbye To Complexity
- Outdated hardware
- Device-centric access control
- SSL-VPNs
- DNS Filters
- A separate secure web gateway
- Paid MFA tools
- On-premise firewalls (in some cases)
Say Hello To Timus
- Cloud-only operations
- Streamlined security stack
- User and identity-based access control
- Up to 50 hours/month saved in IT hours
- Up to 30% savings in support tickets
- Up to 70% reduction in TCO
Everything You Need in One Platform
Always-on, Zero-Click Encrypted Access to Resources
Zero Trust Network Access (ZTNA)
Dynamic Cloud Firewall (FWaaS)
Dedicated Static IPs for SaaS App Security
Secure Web Gateway for Phish-free Browsing and More
Advanced Device Posture Checks
Secure Web Gateway
Protect users from web-based threats by filtering malicious content and enforcing safe, compliant browsing policies
Blazing-Fast
Dedicated Gateways
Ensure ultra-low latency and high-speed performance through global, 1 Gbps gateways optimized for fast connectivity
Site-to-site Connections
Connect multiple office sites securely under one virtual network via unlimited IPSec tunnels, enabling consistent access control and simplified network management
Rich Reporting
and Audit Trails
Automatically generate detailed reports and audit logs as a trusted advisor to your clients. Deep visibility, compliance, and streamlined incident response across the network
Best Support in
the Channel
Get unmatched, expert-driven support tailored for MSPs—fast response times, real human help, and deep understanding of your unique business needs
Timus API to Help
Automate Workflows
Integrate and automate security operations, log exports to SIEM of your choice, device management, and reporting using Timus’s powerful, flexible, and developer-friendly API
Real Outcomes, Not Just Features
Explore how Timus solves real-world access and security problems for MSPs
We’re Not Just MSP-Friendly. We’re MSP-Focused.
Timus SASE was built from the ground up to serve the channel.
No bolt-ons. No enterprise leftovers. Real passion for MSP success.
Experience the Timus Difference
- The only dedicated SASE
vendor, built for the channel
- Multi-tenant
architecture
- Per-user pricing & full
client separation
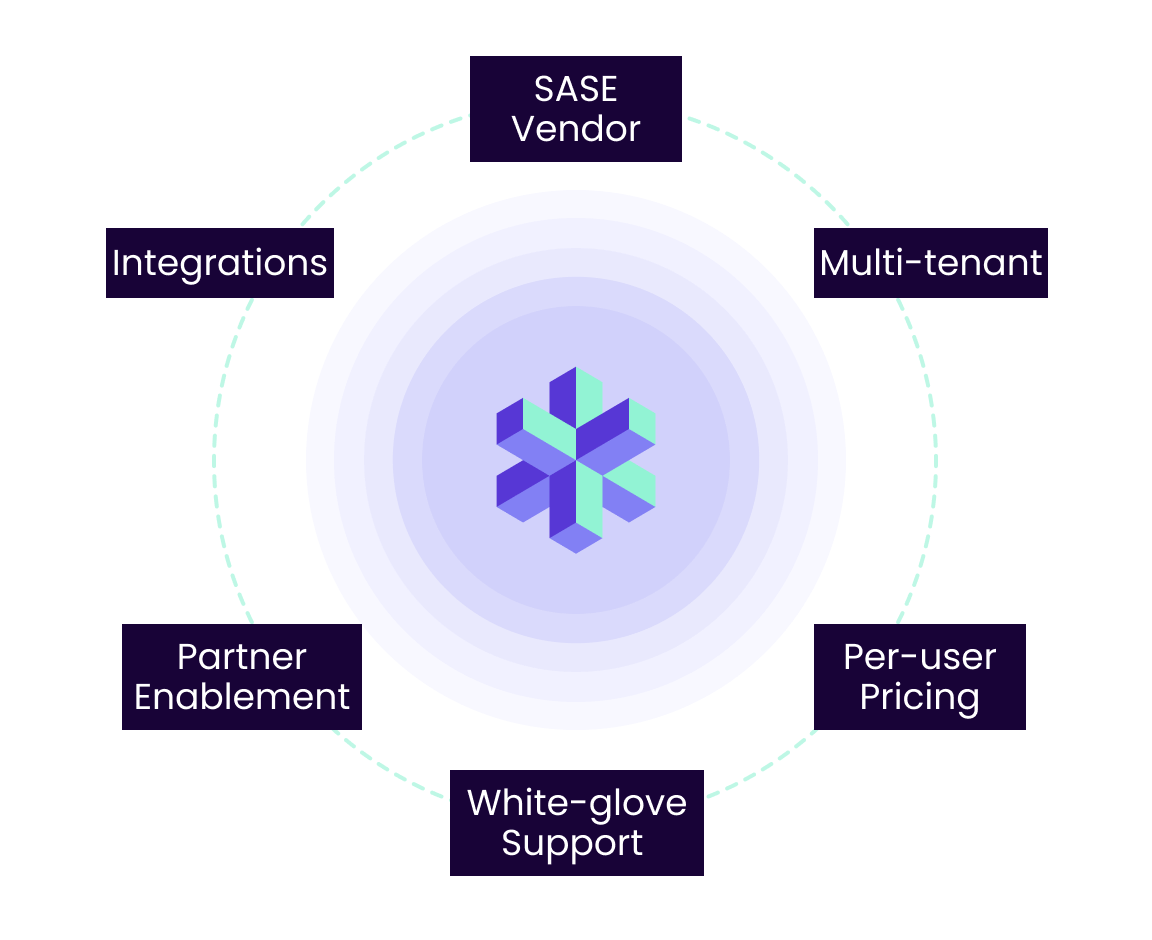
- Partner enablement tools (sales decks, co-branded assets, onboarding)
- Robust integrations, a “better together” vendor
- White-glove deployment & best-in class support
Built on Trust. Backed by Compliance.
Timus is ISO 27001 certified and SOC 2 Type 2 compliance — demonstrating our commitment to earning and maintaining your trust through proven security practices.

Timus Fits Right Into Your Stack
Timus integrates seamlessly with the platforms you already rely on
You Could Be Live in Under 30 Minutes
30 Days. Zero Cost. Cancel Anytime.
Experience the full power of Timus with real clients, real users, and real protection. No demo environments. Just results.
- Support included
- Full access to all premium features
- Cancel anytime
You could be live in 00:29:00
30-day free with a satisfaction guarantee
MSP Referral Program
Introduce your peers to our cutting-edge SASE / ZTNA solution and earn rewards along the way. It’s a great way to share the Timus value and get rewarded for it!
Learn, Explore, Secure
MSPs Are Moving to Modern Security. Are You?
Secure your clients, grow your revenue, and simplify your stack with Timus SASE.
30-day free with satisfaction guarantee